TryHackMe | Ignite | Writeup
Hey Guys, I’m System.Exit and in this writeup we’re gonna learn how to solve the tryhackme machine Ignite
You can access the room link from Here
"Ignite" is a straightforward challenge on TryHackMe. In this exercise, you will engage in basic enumeration and delve into FUEL CMS, discovering how to exploit it to gain access to the server.
Deploy the machine!
Let’s try with basic nmap to see open ports
 | |
| Nmap Scan |
The /fuel directory leads to a login form, which (not surprisingly so) can be accessed with the default credentials admin:admin
"Even with this access, I couldn't achieve much in the admin interface. I attempted some file upload techniques, but accessing this page appears to be a rabbit hole. Let's set it aside for now."
Gaining Access to the Machine
Let's check if FUEL CMS has any known vulnerabilities using SearchSploit.
Exploits that enable Remote Code Execution (RCE) are particularly valuable in situations like this. Fortunately, there is an RCE exploit available for FUEL CMS. We can download the exploit script using the following command:
searchsploit -m php/webapps/50477.py
Exploits that enable Remote Code Execution (RCE) are particularly valuable in situations like this. Fortunately, there is an RCE exploit available for FUEL CMS. We can download the exploit script using the following command:
searchsploit -m php/webapps/50477.py
I chose this particular script because it's written in Python 3, a language I'm familiar with, making it easier to modify if needed. However, feel free to use any other scripts that might suit you better.
This script exploits a vulnerability disclosed in CVE-2018-16763, which indicates that FUEL CMS versions ≤ 1.4.1 are susceptible to Remote Code Execution (RCE) due to improper input validation in the `/pages/select` filter parameter and `/preview` data parameter.
Taking a closer look at the script, we can see how it communicates with the server:
I chose this particular script because it's written in Python 3, a language I'm familiar with, making it easier to modify if needed. However, feel free to use any other scripts that might suit you better.
This script exploits a vulnerability disclosed in CVE-2018-16763, which indicates that FUEL CMS versions ≤ 1.4.1 are susceptible to Remote Code Execution (RCE) due to improper input validation in the `/pages/select` filter parameter and `/preview` data parameter.
Taking a closer look at the script, we can see how it communicates with the server:
Since we can execute system commands, we can spawn a reverse shell on the server. In another terminal, let's start listening for connections
Since we can execute system commands, we can spawn a reverse shell on the server. In another terminal, let's start listening for connections
And in the terminal running the exploit, we can send this command to spawn a reverse shell:
First, let's get a better shell:
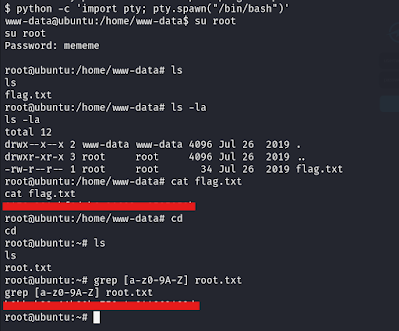
python -c 'import pty; pty.spawn("/bin/bash")' Now we can look around the directories and files to find the user flag: cat /home/www-data/flag.txt
Privilege Escalation
After attempting some basic privilege escalation techniques, I revisited the default landing page we initially found. That's when I noticed something interesting: Let's see if this password works for the root user:









Comments
Post a Comment