Hack The Box - Misc | SecretRezipe | Writeup
SecretRezipe - Challenge Writeup
Hello everyone! Today, we'll go through solving an easy but fun challenge called SecretRezipe.
Challenge Overview:
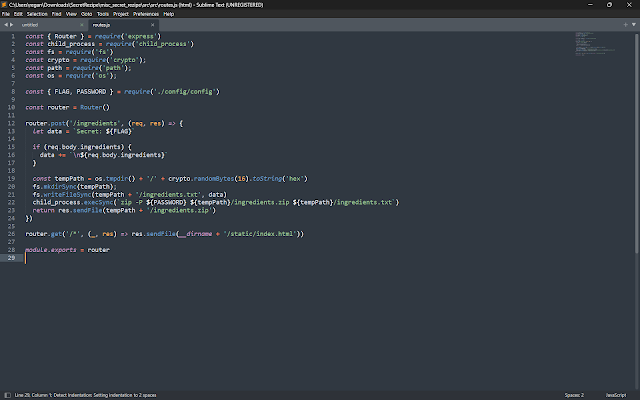
We are given a ZIP file named ingredients.zip, and we know it's encrypted using the ZipCrypto algorithm. Our task is to extract the secret recipe from this archive, but the password is unknown.
The archive is small, containing a file with the path tmp/4b09381268fd861be50e158df8d7f46e/ingredients.txt. The goal is to decrypt this file and retrieve the flag formatted as HTB{}.
Approach:
After analyzing the situation, it’s clear that this is a classic legacy ZIP encryption problem, and we can solve it using a known plaintext attack with the help of the bkcrack tool.

Steps to Solve:
Step 1: Install bkcrack
First, we need to install bkcrack, a tool designed for cracking ZipCrypto encryption. You can download and compile it as follows:
git clone https://github.com/kimci86/bkcrack
cd bkcrack
mkdir build
cd build
cmake ..
makeStep 2: Analyze the ZIP File
We know the file we are looking for inside the ZIP archive is ingredients.txt. We can inspect the contents of the archive with the bkcrack -L command:
./bkcrack -L /home/kali/ingredients.zip
This command will list the encrypted contents of the ZIP file and confirm the path to ingredients.txt.
Step 3: Prepare Known Plaintext
Looking at the challenge description and the file path, we know that the first line in the file will likely contain the string:
Secret: HTB{We can create a file named plain with this known content:
echo "Secret: HTB{" > /home/kali/plainTo ensure it’s correctly formatted, use a hex editor to verify that the plaintext file contains only this text and no extra characters.
Step 4: Perform Known Plaintext Attack
Now, we use bkcrack to perform the known plaintext attack. The command uses the archive, the path to the encrypted file, and the known plaintext to crack the encryption:
./bkcrack -C /home/kali/ingredients.zip -c tmp/4b09381268fd861be50e158df8d7f46e/ingredients.txt -p /home/kali/plain
This will take some time, but eventually, bkcrack will find the encryption keys.
Step 5: Use the Keys to Decrypt
Once the keys are found, we can use them to decrypt the file. Here’s the command to do that:
./bkcrack -C /home/kali/ingredients.zip -c tmp/4b09381268fd861be50e158df8d7f46e/ingredients.txt -k c08a3e7d 4e958ebb b6c07482 -d secret.txtThis will write the decrypted content of ingredients.txt into a new file called secret.txt.
Step 6: Retrieve the Flag
Finally, we can read the contents of the decrypted file to get the flag:
cat secret.txt
The output will be:
Secret: HTB{C***************n}Conclusion:
This challenge might seem tricky at first, but by applying the known plaintext attack method using bkcrack, we were able to retrieve the flag successfully. This was a great opportunity to learn more about legacy ZIP encryption vulnerabilities and how to exploit them using known plaintext.








Comments
Post a Comment