Hack The Box - Reversing | Golfer - Part 1 | Writeup
When you try running the binary, nothing seems to happen. If you dive deeper into the assembly code, you'll notice it’s sparse — not much is going on.
Upon analyzing it with radare2, I observed a significant jump right after the first line, bypassing several functions all the way to
0x08000127. This is where the fun begins. It’s clear that some critical functionality is being skipped, and we need to prevent this jump from happening.
Step 1: Analyze the Code
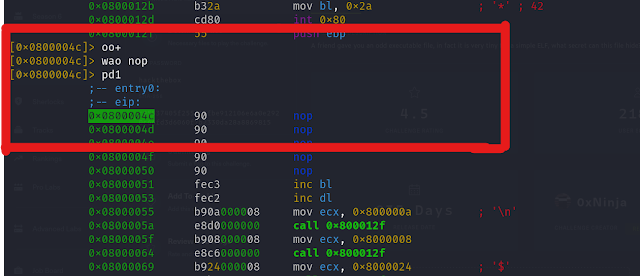
Starting at the address 0x0800004c, we need to modify the assembly to ensure it doesn't skip over key functions. The solution is simple: change the jump (jmp) instruction.
Step 2: Modify the Jump Instruction
Instead of removing the function call entirely, we replace it with nop, an instruction that does nothing. This ensures that the program doesn't skip over important code but also doesn't execute unnecessary operations.
Step 3: Using radare2
To make the modification, open the binary in radare2:
Step 4: Confirm the Changes
After modifying the code, you can check if the change was successful by using the pd1 command to disassemble the next instruction. If everything looks correct, exit with q and run the binary again.
Step 5: Enjoy the Flag
After running the file! The flag is now available.






Comments
Post a Comment