Bypassing 2FA to Impersonate Users on Drugs.com | Bug Bounty
Introduction
Hey Security Enthusiasts!
A
serious authentication flaw was recently discovered on Drugs.com,
allowing attackers to bypass Two-Factor Authentication (2FA) and
impersonate legitimate users. This vulnerability exposed user accounts
to takeover risks due to improper session handling and weak email
verification.
What Happened?
During security testing, researcher (duk3_) found that Drugs.com did not properly verify email ownership during account changes. This enabled an attacker to hijack accounts without requiring 2FA re-authentication.
Steps to ReproduceRegister an Account:
- Register an Account
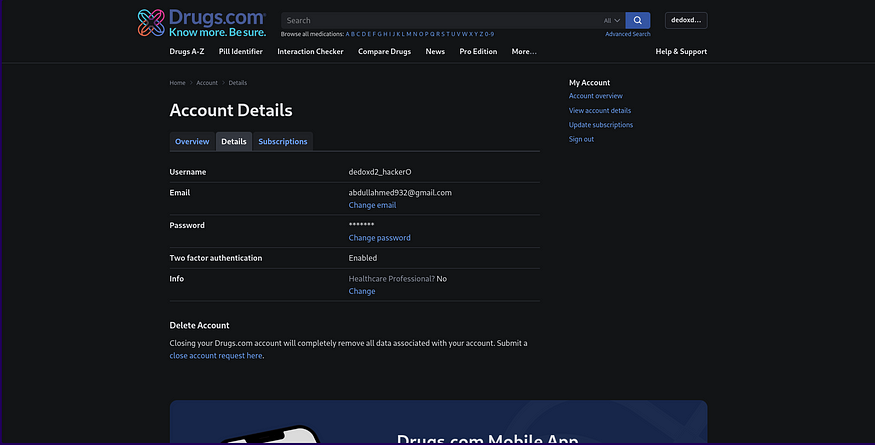
- Sign up on Drugs.com with an attacker-controlled email.
- Complete OTP verification and select “Trust this device for 1 month.”
2. Change Email to Victim’s Email
- Navigate to Account Details.
- Change the registered email to the victim’s email.
- Since the attacker’s session remains active, they retain control of the account.
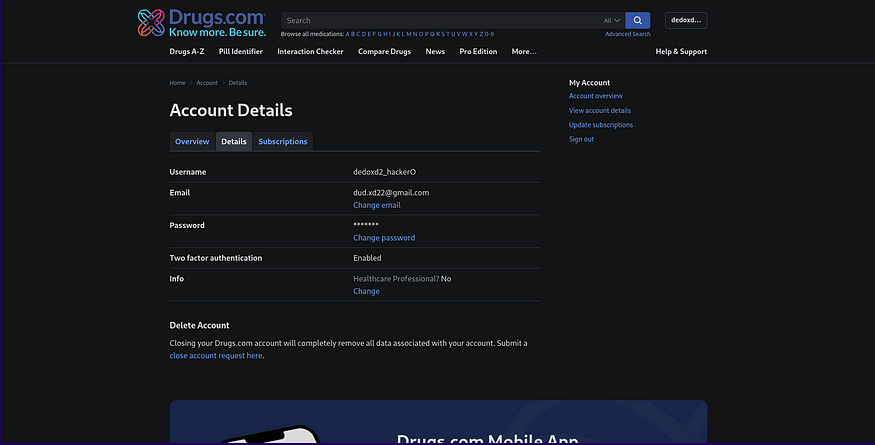
3. Bypass 2FA
- Log out and log back in — 2FA is no longer required.
- Cycle between the attacker’s and victim’s email to maintain persistent access.
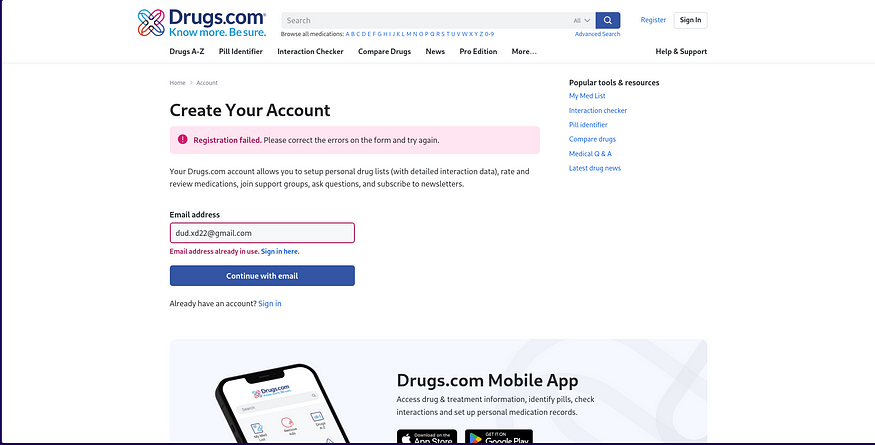
4. Impact on Victim
- The victim is locked out when attempting to register, as their email is “already in use.”
- The attacker continues to impersonate them without detection.
Report Details
Reported to: Drugs.com
Report ID: #2885636
Severity: High (7.5)
Weakness:Improper Authentication — Generic
Final Thoughts
Thanks to duk3_ for discovering this vulnerability and earning well-deserved recognition in the Security Hall of Fame. Kudos to him for responsible disclosure!Stay secure and happy hacking! 🚀🔐



Comments
Post a Comment